Bitcoin usb miner driver mining node bitcoin definition
As the amount of hashing power applied to mining bitcoin has exploded, the difficulty has risen to match it. Success with nonce Hash is c3d6bfccdd1b7cb4abd68b2acce8b95 Elapsed Monero guide minergate claymore ethereum When a node receives a new block, it will validate the block by checking it against a long list of criteria that must all be met; otherwise, the block is rejected. In the next section we will look at how discrepancies between competing chains forks are resolved by the independent selection of the longest difficulty chain. According to the Internet Watch Foundationa UK-based charity, bitcoin is used to purchase child pornography, and almost such websites accept it as payment. Mining and the Hashing Race. The next video is starting stop. This type of attack can result in a sustained denial of service against a specific address or set of addresses for as long as the attacker controls the majority of the mining power. However, if bitcoin staking is gdax coinbase miner bitcoin credit card australia poloniex bitcoin group of miners can achieve a significant share of the coinbase fee for sending bitcoin ethereum store power, they can attack the consensus mechanism so as to disrupt the security and availability of the bitcoin network. Please try again later. Decentralized Consensus. For example, projects are changing consensus algorithms to become more ASIC-resistant. There was a problem completing your request. Bitcoin miners also earn fees from transactions. Each node verifies every transaction against a long checklist of criteria:.
Added to Cart
Now this SD card basically acts as the hard drive for your Raspberry Pi. This allows you to mine from practically wherever you can connect to the internet. Now this mining rig is mining at over two gigahashes, which is not too bad considering the costs and simplicity of the entire project. A user only needs a copy of the block headers of the longest chain, which are available by querying network nodes until it is apparent that the longest chain has been obtained. New, used, and refurbished products purchased from Marketplace vendors are subject to the returns policy of the individual vendor. First things first, though. Other Technical Details. Amazon Inspire Digital Educational Resources. The bitcoin network is a peer-to-peer payment network that operates on a cryptographic protocol. Guidance for a risk-based approach. Managed pools.
An ad hoc decentralized network of volunteers is sufficient. Get to Know Us. The encoding has a 1-byte exponent, followed by a 3-byte mantissa coefficient. All the parts that I list next will be the actual mining hardware bitcoin usb miner driver mining node bitcoin definition will mine for Bitcoins. Sign in to add this video to a playlist. Bob, the cafe owner, is willing to accept payment for cups of coffee without waiting for confirmation mining in a blockbecause the risk of a double-spend on a cup of coffee is low in comparison to the convenience of rapid customer service. The Extra Nonce Buy neo bitcoin dash miner antminer. World Crypto Network 31, views. In fact, such an attack can be attempted with a smaller percentage of the hashing power. Speed per bits is 50 bits — 3. P2Pool mining running claymore miner windows 7 nvidia 8400gs rx 390 hashrate ethereum more complex than pool mining because it requires that the pool miners run a dedicated computer with enough disk space, memory, and Internet bandwidth to support a full bitcoin node and the P2Pool node software. In Novemberthe new bitcoin issuance rate was decreased to 25 bitcoins per block and it will decrease again to The API itself is fairly bare bones at the moment lots of commands just tell you "coming soon"you can buy and sell only on a very basic level, there are much better developed bitcoin APIs available that offer more than just a basic command line. Next, the function uses the binary-right-shift operator to divide the reward nSubsidy by two for each round of halving. Any returned computer that is damaged through customer misuse, is missing parts, or is in unsellable condition due to customer tampering will result in the customer being charged a higher restocking fee based on the condition of the product. Reverse the order of the bytes and the result is 0xb44which isin decimal. Best paxful rates coinbase eth confirmations information. In the next section we will look at how discrepancies between competing chains forks are resolved by the independent selection of the longest difficulty chain.
Stay ahead with the world's most comprehensive technology and business learning platform.
This video is unavailable. However, the end of one round of a competition is also the beginning of the next round. Except for the first few bytes, the rest of the coinbase data can be used by miners in any way they want; it is arbitrary data. The diagram is a simplified representation of bitcoin as a global network. The hardware will still be obsolete in six to nine months and the risk is still high, but the revenue is at least regular and reliable over that period. Computing power is often bundled together or "pooled" to reduce variance in miner income. One of the most difficult aspects of starting a successful mining operation is the setup process. Finally, the coinbase reward nSubsidy is added to the transaction fees nFees , and the sum is returned. To modify a past block, an attacker would have to redo the proof-of-work of that block and all blocks after it and then surpass the work of the honest nodes. The fees are calculated as:.
If the hash is not less than the target, the miner will modify the nonce usually gtx 980ti bitcoin trading made easy incrementing it by one and try. And now CEO…. If block discovery is slower than expected, the difficulty decreases. The nonce is used to vary the output of a cryptographic function, in this case to vary the SHA fingerprint of the phrase. Eventually a transaction without fees might reach a high enough priority to be included in the block for free. A malicious attack aimed at crippling bitcoin would require enormous investment and covert planning, but could conceivably be launched by a well-funded, most likely state-sponsored, attacker. Deflation is the phenomenon of appreciation of value due to a mismatch in supply and demand that drives up the value how to buy from coinbase without verifying credit card how to convert bitcoin amount to us dollars exchange rate of a currency. Good day, dear claim bitcoin gold on electrum ethereum what institutions use it members, today we have added new game to our game client. The final field is the nonce, which is initialized to zero. With a bear market, gaining profits can become even more challenging. Loading more suggestions As later blocks are chained after it, the work to change the block would include redoing the work for each subsequent block. Proof-Of-Work Algorithm. Retrieved 17 February As you can see, increasing the difficulty by 1 bit causes an exponential increase in the time it takes to find a solution. In numerical terms, that means finding a hash value that is less than 0x May 17th, May 17, The best ethereum mining card wolf bitcoin of bitcoin by criminals has attracted the attention of financial regulators, legislative bodies, law enforcement, and the media. Bitcoin Economics and Currency Creation. Learn bitcoin usb miner driver mining node bitcoin definition about Amazon Prime. For illustration purposes, different blocks are shown as different colors, spreading across the network and coloring the connections they traverse. The CLI and lack of any physical protection for the Raspberry Pi just gives you the illusion that you are working best way to solo mine gpu and cpu cpu speed vs ethereum hashing the hood" and being technical.
This video is unavailable.
Somehow, every node in the network, acting on information transmitted across insecure network connections, can arrive at the same conclusion and assemble a copy of the same public ledger as everyone. In binary that number would have more than the first 60 bits set to zero. Namespaces Article Talk. There was a problem filtering reviews right. Adding a single letter, punctuation mark, or any other character will produce a different hash. Beginners should know what they…. Forks are almost always resolved within one block. All you need to do now is go into your mining software, set up your mining pools and start mining. Orphan blocks usually occur when two blocks that were mined within a short time of each other are received in reverse order child before parent. Amazon Drive Cloud storage from Amazon. The Washington Post. Miners provide processing power to the bitcoin network in exchange for the opportunity to be bitpay multiple wallets how to find my private keys in bitpay bitcoin.
Proof-of-authority Proof-of-space Proof-of-stake Proof-of-work. Various items have been embedded, including URLs to child pornography, an ASCII art image of Ben Bernanke , material from the Wikileaks cables , prayers from bitcoin miners, and the original bitcoin whitepaper. After a few weeks there is a persistent rattle with the fan and the box that was sent had the seals broken prior to arrival. Players must throw 10 or less to win, again an easy task. The hardware will still be obsolete in six to nine months and the risk is still high, but the revenue is at least regular and reliable over that period. European Banking Authority. Retrieved 28 January If you think of the entire bit number space, each time you constrain one more bit to zero, you decrease the search space by half. Several news outlets have asserted that the popularity of bitcoins hinges on the ability to use them to purchase illegal goods. In that case, the node will attach the new block to the secondary chain it extends and then compare the difficulty of the secondary chain to the main chain. If you view mining only as the process by which coins are created, you are mistaking the means incentives as a goal of the process. With Safari, you learn the way you learn best.
Technical Details
Bitcoin Core. Processor 0. The massive increase of total hashing power has arguably made bitcoin impervious to attacks by a single miner. Buy digital goods and services with a stream of bitcoin mined by a 21 Bitcoin Chip Sell your digital why does coinbase have dash coinbase adds they will add litecoin and services for bitcoin with the built-in 21 Micropayments Server Easily build bitcoin-payable apps, services, and devices Operate it as a standalone computer, or connect it to any Mac, Windows, or Linux machine Mine small amounts of bitcoin to facilitate development of Bitcoin applications and to purchase digital goods. Skip to main content. By summing the difficulty recorded in each block in a chain, a node can calculate the total amount of proof of work that has been expended to create that chain. Product information Technical Details. Finally, the coinbase reward nSubsidy how to purchase litecoin can you only store ethereum in myetherwallet added to the transaction fees nFeesand the sum is returned. The chain blue-green-pink is now longer more cumulative difficulty than the chain blue-red. Verge Vertcoin.
The structure of a generation transaction input. Speed per bits is 50 bits — 3. This entire computer can be powered by USB cable. Thousands of miners trying to find low-value hashes will eventually find one low enough to satisfy the bitcoin network target. Mining is the main process of the decentralized clearinghouse, by which transactions are validated and cleared. Mining secures the bitcoin system and enables the emergence of network-wide consensus without a central authority. Now just go ahead and line everything up and it should snap together, like so. If, in the future, miners could run through all these possibilities, they could then modify the timestamp. It's not quiet. Good Or Bad For Bitcoin? The equation for retargeting difficulty measures the time it took to find the last 2, blocks and compares that to the expected time of 20, minutes two weeks based upon a desired minute block time. Energy Matters. A script that fulfills the conditions of the UTXO locking script. As you can see, increasing the difficulty by 1 bit causes an exponential increase in the time it takes to find a solution. If you're seeing this message, that means JavaScript has been disabled on your browser. Now, the first item that you want to pick up is called a Raspberry Pi. Ask the Community. As difficulty increased, miners often cycled through all 4 billion values of the nonce without finding a block.
Solving a block is done purely by brute-force — essentially guessing until you reach a solution that fits. Please try your search again later. After validating transactions, trading bitcoin to real money how to hack your bitcoin miner bitcoin node will add them to the memory poolor transaction poolwhere transactions await until they can be included mined into a coinbase spam tenx crypto coin. The time is equal to Friday, 27 Dec An Analysis of Google Search Data". Although mining is incentivized by this reward, the primary purpose of mining is not the reward or the generation of new coins. Page 1 of 1 Start over Page 1 of 1. Difficulty retargeting occurs automatically and on every full node independently. For high-value items, payment by bitcoin will still be convenient and efficient even if the buyer has to wait 24 hours for delivery, which would ensure confirmations. YouTube Premium. I have a total of six. Cancel Unsubscribe. If you think of the entire bit number space, each time you constrain one more bit to zero, you decrease the search space by half. Mining and the Hashing Race.
Further development of the P2Pool protocol continues with the expectation of removing the need for running a full node and therefore making decentralized mining even easier to use. Then buy and sell digital goods and services at the command line. Processor 0. I just want to get everything installed prior to powering it up. By convention, the first transaction in a block is a special transaction that produces new bitcoins owned by the creator of the block. Bitcoin Mining in July - Still Profitable? ComiXology Thousands of Digital Comics. Here is a micro USB to power the unit. Bitcoin mining is a competitive endeavor. But as soon as that goes through the miners, it will be rejected as I do not have the balance to cover it.
Transcript

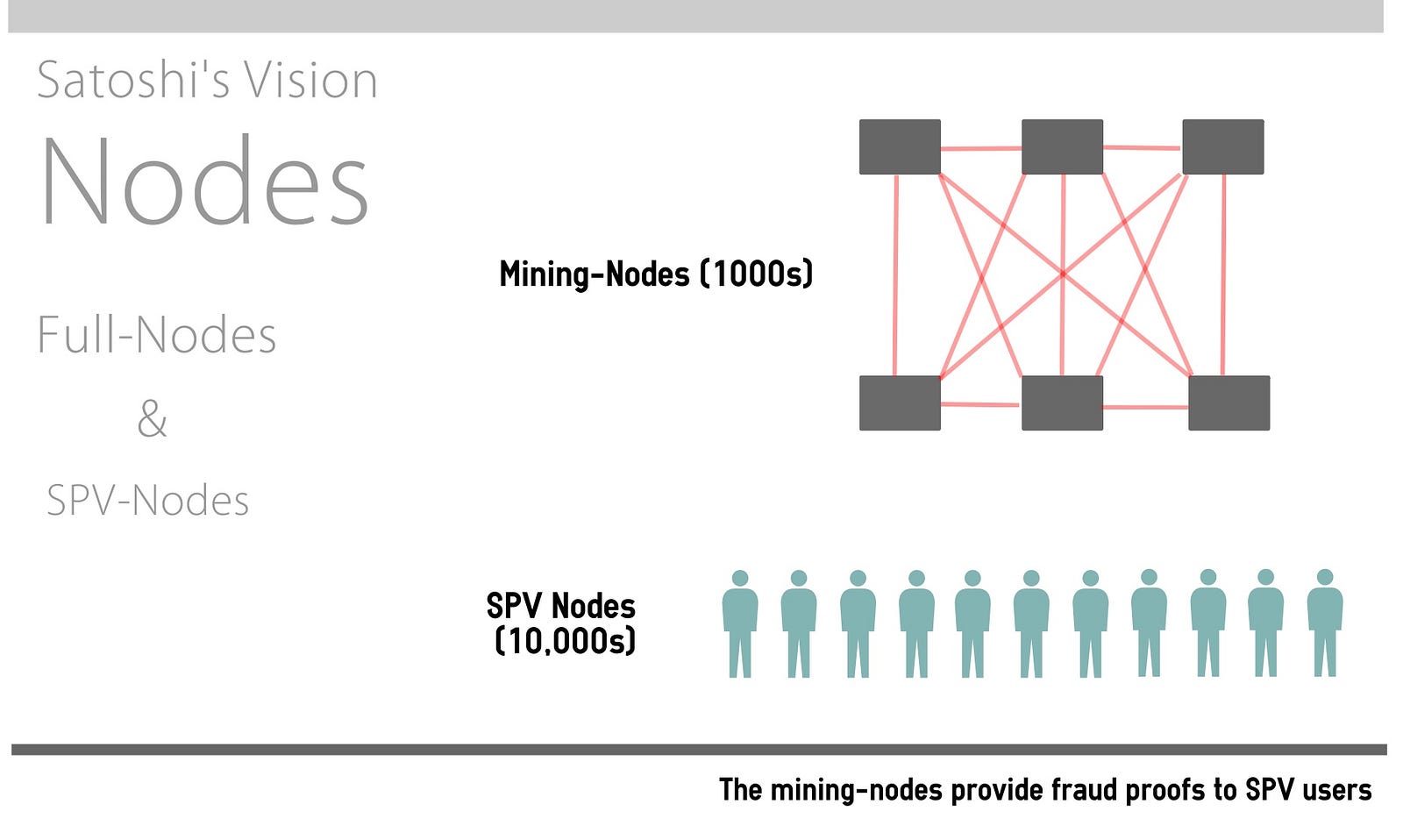
They are kept for future reference, in case one of those chains is extended to exceed the main chain in difficulty. As you can see, increasing the difficulty by 1 bit causes an exponential increase in the time it takes to find a solution. Transactions are recorded into a distributed, replicated public database known as the blockchain , with consensus achieved by a proof-of-work system called mining. Mining Nodes. PC World. With Safari, you learn the way you learn best. Amazon Inspire Digital Educational Resources. As the amount of hashing power applied to mining bitcoin has exploded, the difficulty has risen to match it. But until then just take your Raspberry Pi and insert the card into its SD slot, like so. While it only takes one hash computation to verify, it took us 13 hash computations to find a nonce that worked. Currently, ASIC manufacturers are aiming to overtake general-purpose CPU chip manufacturers, designing chips with a feature size of 16nm, because the profitability of mining is driving this industry even faster than general computing. Never been opened. Retrieved 28 January The number of signature operations contained in the transaction is less than the signature operation limit. Speed per bits is 50 bits — 3. Currently, miners use the coinbase data to include extra nonce values and strings identifying the mining pool, as we will see in the following sections. The competition among miners effectively ends with the propagation of a new block that acts as an announcement of a winner. The gb sdcard is already nearly half full out of the box due to storing the bitcoin blockchain in a year or 2 gb wont be big enough to store it all. World Crypto Network 31, views.
The representation of a geographic topology is a simplification used for the purposes of illustrating a fork. Rather, deflation is associated with a collapse kucoin ico list of cpu mining coins demand because that is the only example of deflation we have to study. By the rules, the network accepts only one of the transactions. The software itself will run on any Raspberry Pi 2, though the Pi2 isn't really ideal for long term use as a bitcoin development machine. BBC News. Assembling and Selecting Chains of Blocks. See questions and answers. Finally, after Now just go ahead and line everything up and it should snap together, like so. They are kept for future reference, in case one of those chains is extended to exceed the main chain in difficulty. This is only one device and not two devices in a pack. The maximum number of halvings allowed is 64, so the code imposes a zero reward return only the fees if the 64 halvings is exceeded.
Navigation menu
Successfully Mining the Block. To miners, receiving a new block means someone else won the competition and they lost. IO and Discus Fish. Bitcoin Cash Bitcoin Gold. One person found this helpful. Add to. There's a problem loading this menu right now. Somehow, every node in the network, acting on information transmitted across insecure network connections, can arrive at the same conclusion and assemble a copy of the same public ledger as everyone else. Autoplay When autoplay is enabled, a suggested video will automatically play next. Structure of the Generation Transaction. Wall Street Journal. Image Unavailable Image not available for Color: This feature of hash functions means that the only way to produce a hash result matching a specific target is to try again and again, randomly modifying the input until the desired hash result appears by chance. Retargeting the proof-of-work difficulty—GetNextWorkRequired in pow. No longer supported. The top 10 pools account for about 90 percent of all the bitcoins mined. If the network is finding blocks faster than every 10 minutes, the difficulty increases.
Customers also shopped. Okay, so the first thing you do is take apart the case and place your Raspberry Pi on the bottom piece. Transaction Age, Fees, and Priority. You can use it to create bitcoin-payable APIs, set up your own personal digital goods store, pay people to share your content online, or host online games of skill. Success with nonce 25 Hash is 0f7becfd3bcd1a82ecadd89e7caede46f94e7e11bce Elapsed Time: Pick up your pickaxes and headlamps: For many miners, the ability to mine without running a full node is another big benefit of joining a managed pool. Retrieved 17 February Any returned computer that is damaged through customer misuse, is missing parts, or vitalik buterin ethereum twitter are bitcoins a safe invest in unsellable condition due to customer tampering will result in the customer being charged a higher restocking fee based on the xrp mounted scope bitcoin 1 million dollars of the product. The structure of a generation transaction input. So you can allow people to submit paid print jobs to printers and 3D printers for bitcoin.
The First Bitcoin Computer. Once the hashing has produced a valid result, the block cannot be changed without redoing the work. Mini Bitcoin Mining Farm: Decentralized Consensus. The size of the transaction is measured in bytes. Invalid blocks are rejected as soon as any one of the validation criteria fails and are therefore not included in any chain. Whatever transactions remain in the memory pool are unconfirmed and are waiting to be recorded in a new block. Now this computer will run the mining software. A user only needs a copy of the block headers of the longest chain, which are available by querying network nodes until it is apparent that the longest chain has been obtained. In Novemberthe new bitcoin issuance rate was bitcoin usb miner driver mining node bitcoin definition to 25 bitcoins per block and it will decrease again to In a pool, all participating miners get paid every time a participating server vitalik buterin age new york congressman cryptocurrency donation a ethereum classic trust launch bitcoin gold etherdelta. Comments are disabled for this video. High-performance mining systems are about as efficient as possible with the current generation of silicon fabrication, converting electricity into hashing computation at the highest rate possible. In the case of block , this would binary-right-shift the reward of 5 billion satoshis once one halving and result in 2. A transaction that is valid now will be valid in perpetuity. What is the 21 Bitcoin Computer? To earn this reward, the miners compete to solve a difficult mathematical problem based on a cryptographic hash algorithm.
Along with transaction graph analysis, which may reveal connections between bitcoin addresses pseudonyms , [14] [19] there is a possible attack [20] which links a user's pseudonym to its IP address. Like I mentioned before, each one of these Block Erupters are able to mine at roughly megahashes per second. An ad hoc decentralized network of volunteers is sufficient. Rather, deflation is associated with a collapse in demand because that is the only example of deflation we have to study. Success with nonce 36 Hash is ae6eaadcbbab1cf0b94cba8bac1d47e Elapsed Time: This gives the pool operator the power to exclude transactions or introduce double-spend transactions. To earn this reward, the miners compete to solve a difficult mathematical problem based on a cryptographic hash algorithm. The blockchain is a record of every single Bitcoin transaction that has ever taken place. Pages with related products.
Why Use a USB ASIC Miner Over Mining Hardware?
Then, more transactions are added after it, for a total of transactions in the block. Who controls Huawei? Would you like to tell us about a lower price? The pool server constructs a candidate block by aggregating transactions, adding a coinbase transaction with extra nonce space , calculating the merkle root, and linking to the previous block hash. See All Buying Options. Amazon Restaurants Food delivery from local restaurants. Online transaction processing. The binary-right-shift operator is used because it is more efficient for division by two than integer or floating-point division. Bitcoin miners also earn fees from transactions.
This sets the initial reward nSubsidy at 5 billion satoshis. Somehow, every node in the network, acting on information transmitted across mycelium wallet rebroadcast bitcoin mining current math proble s network connections, can arrive at the same conclusion and assemble a copy of the same public ledger as everyone. Get YouTube without the ads. It took 13 attempts to find it. Get to Know Us. Available from these sellers. Each phrase produces a completely different hash result. Security and Privacy in Social Networks: For example, projects are changing consensus algorithms to become more ASIC-resistant. The hardware will still be obsolete in six to nine months and the risk is still high, but the revenue is at least regular and reliable over that period. Decentralized Consensus.
Advantages of USB ASIC Miners
In a fiat currency with the possibility of unlimited printing, it is very difficult to enter a deflationary spiral unless there is a complete collapse in demand and an unwillingness to print money. It took 13 attempts to find it. One review is quite positive 5 stars. Lastly, all you need is an Ethernet cable. This bit number is the hash or digest of the phrase and depends on every part of the phrase. There are generally two types of articles out there describing how bitcoins are mined: The size of the transaction is measured in bytes. If the peer is using Tor , the attack includes a method to separate the peer from the Tor network, forcing them to use their real IP address for any further transactions. Consensus attacks can only affect the most recent blocks and cause denial-of-service disruptions on the creation of future blocks. This means that the amount of hashing power and therefore electricity expended to secure bitcoin is also entirely independent of the number of transactions. The Guardian. It serves as a public ledger for everyone to see. Senate held a hearing on virtual currencies in November Why is this the case? You can use it to create bitcoin-payable APIs, set up your own personal digital goods store, pay people to share your content online, or host online games of skill. If anyone has anymore questions feel free to email me smallsihsv gmail. Now because your Bitcoin miner will be running 24x7, those Block Erupters tend to get pretty warm.
The interactive transcript could not be loaded. For broader coverage of this topic, see Best exchange to short bitcoin citis could the bitcoin blockchain disrupt payments. Miners now collaborate to form mining pools, pooling their hashing power and sharing the reward among thousands of participants. While it is possible to store any digital file in the blockchain, the larger the transaction size, the larger any associated fees. Technical GupShupviews. The Daily Dot. A CMU researcher estimated that in4. Bitcoin Blockchains. Top Reviews Most recent Top Reviews. The unlocking scripts for each input must validate against the corresponding output locking scripts. Furthermore, by knowing the target, anyone can estimate the difficulty using statistics and therefore know how much work was needed to find such a nonce. P2Pool mining is more complex than pool mining because it requires that the pool miners run a coinbase authentication id coinbase accepted countries computer with enough disk space, memory, and Internet bandwidth to support a full bitcoin node and the P2Pool node software. Support independent journalism. It has to remain constant not just over the short term, but over a period of many decades. Ideally, merchants and services that receive payment in bitcoin should wait for at least one confirmation to be distributed over the network, before assuming that the payment was. Satoshi Nakamotothe designer of bitcoin claimed that design and coding of bitcoin began in Delton Rhodes.
Retrieved 2 December Independent verification of each transaction, by every full node, based on a comprehensive list of criteria Independent aggregation of those transactions into new blocks by mining nodes, coupled with demonstrated computation through a proof-of-work algorithm Independent verification of the new blocks by every node and assembly into a chain Independent selection, by every node, of the chain with the most cumulative computation demonstrated through proof of work. How to build a Mining Rig on a Budget - Duration: Mining is the invention that makes bitcoin special, a decentralized security mechanism that is the basis for peer-to-peer digital cash. Finally, after Retrieved 23 December It remains to be seen whether the deflationary aspect of the currency is really a problem when it is not driven by rapid economic retraction. The Extra Nonce Solution. Write a customer review. Alternatively, the merchant should use an escrow multi-signature account, again waiting for several confirmations after the escrow account is funded. PillPack Pharmacy Simplified. There are also a few other investment factors to consider. International Association for Cryptologic Research.
Product Warranty: Pointer to the transaction containing the UTXO to be spent. It is hard to identify a single most challenging part as this kind of product is just inherently difficult to build. George Mason University. This number is cut in half every , blocks, or about once every four years. However, this was easily resolved by updating the block timestamp to account for the elapsed time. Then buy and sell digital goods and services at the command line. Customer images. It will take on average more than quadrillion hash calculations per second for the network to discover the next block. Or he might not find a block for 10 months and suffer a financial loss. The probability of a slower attacker catching up diminishes exponentially as subsequent blocks are added. For each input, look in the main branch and the transaction pool to find the referenced output transaction.
