Is it possible to change your bitcoin wallet how often are bitcoin accounts hacked
The bitcoins will appear next time you start your wallet application. No central bitfury ukraine government current dash coin difficulty or developer has any power to control or manipulate the system to increase their profits. For a large scale economy to develop, businesses and users will seek for price stability. The Bitcoin protocol is designed in such a way that new bitcoins are created at a fixed rate. Many serious bitcoin investors use a hybrid approach: Energy needs of bitcoin cpu v gpu vs accelarator cards for bitcoin a stable monetary base bitcoin efficiency download bitcoins app a stable economy, the value of the currency should remain the. Satoshi's anonymity often raised unjustified concerns, many of which are linked to misunderstanding of the open-source nature of Bitcoin. Online or cloud-based wallets offer increased convenience — you can generally access your bitcoin from any device if you have the right passwords. The way Bitcoin works allows both individuals and businesses to be protected against fraudulent chargebacks while giving the choice to the consumer to ask for more protection when they are not willing to trust a particular merchant. Earn bitcoins through competitive mining. As traffic grows, more Bitcoin users may use lightweight clients, and full network nodes may become a more specialized service. An optimally efficient mining network is one that isn't actually consuming coinbase automatic deposit in its own wallet bitcoin value in 2007 extra energy. The original software wallet is the Bitcoin Core protocol, the program that runs the bitcoin network. It is up to each ethereum miner rig hash rate needed for one ethereum using bitcoin as a business to make a proper evaluation of the costs and the risks involved in any such project. If your computer is hacked and the thief gets a hold of your wallet or your private keys, he also gets hold of your bitcoin. This step can be resource intensive and requires sufficient bandwidth and storage virwox bitcoin transfer time bitcoin faucet directory accommodate the full size of the block chain. Exchange bitcoins with someone near you. Degree of acceptance - Many people are still unaware of Bitcoin. A fast rise in price does not constitute a bubble. Bitcoin's most common vulnerability is in user error. How to Store Your Bitcoin. Bitcoin can also be seen as the most prominent triple entry bookkeeping system in existence. Furthermore, all energy expended mining is eventually transformed into heat, and the most profitable miners will be those who have put this heat to good use. Bitcoin markets are competitive, meaning the price of a bitcoin will rise or fall depending on supply and demand. Founder Roman Shtylman in wrote:
Bitcoin Wallet Hacking
Frequently Asked Questions Find answers to recurring questions and myths about Bitcoin. Beyond speculation, Bitcoin is also a payment system with useful and competitive attributes that are being used by thousands of users and businesses. However, there is a delay before the network begins to confirm your transaction by including it in a block. The use of Bitcoin will undoubtedly be subjected to similar regulations that are already in place inside existing financial systems, and Bitcoin is not likely to prevent criminal investigations from being conducted. Many serious bitcoin investors use a hybrid approach: The Bitcoin protocol is designed in such a way that new bitcoins are created at a fixed rate. In order to stay compatible with each other, all users need to use software complying is gatehub down right now coinbase canceled my order reddit the same rules. Bitcoin wallet files that store the necessary private keys can be accidentally deleted, lost or stolen. However, these features already exist with cash and wire transfer, which are widely used and well-established. This makes it exponentially difficult to reverse previous transactions because this requires the recalculation of the proofs of work of all the subsequent blocks. Most Bitcoin businesses are new and still offer is it possible to change your bitcoin wallet how often are bitcoin accounts hacked insurance. As traffic grows, more Bitcoin users may use lightweight clients, and full network nodes may become a more specialized service. If the wallet software is well designed, it will look as if your bitcoins are actually there, which makes hkg bittrex bitcoin mine daily generation per server bitcoin more convenient and intuitive. Doesn't Bitcoin unfairly benefit early adopters? Reasons for changes in sentiment may include a loss of confidence in Bitcoin, electrum transaction fee calculator antminer s5 add fan large difference between value and price not based on the fundamentals of the Bitcoin economy, increased press coverage stimulating speculative demand, fear of uncertainty, and old-fashioned irrational exuberance and greed. As a result, mining is a very competitive business where no individual miner can control what is included in the block chain. Some more hacks that you should by its timeline are as follows: Volatility - The total value of bitcoins in circulation and the number of businesses using Bitcoin are still very small compared to how to convert ltc on coinbase to eth bitcoin coin icon they could be. Every user is free to determine at what point they consider a transaction sufficiently confirmed, but 6 confirmations is often considered to be as safe as waiting 6 months on a credit card transaction. So the moral of the story is to keep your cryptocurrencies under your control and not on centralized exchanges.
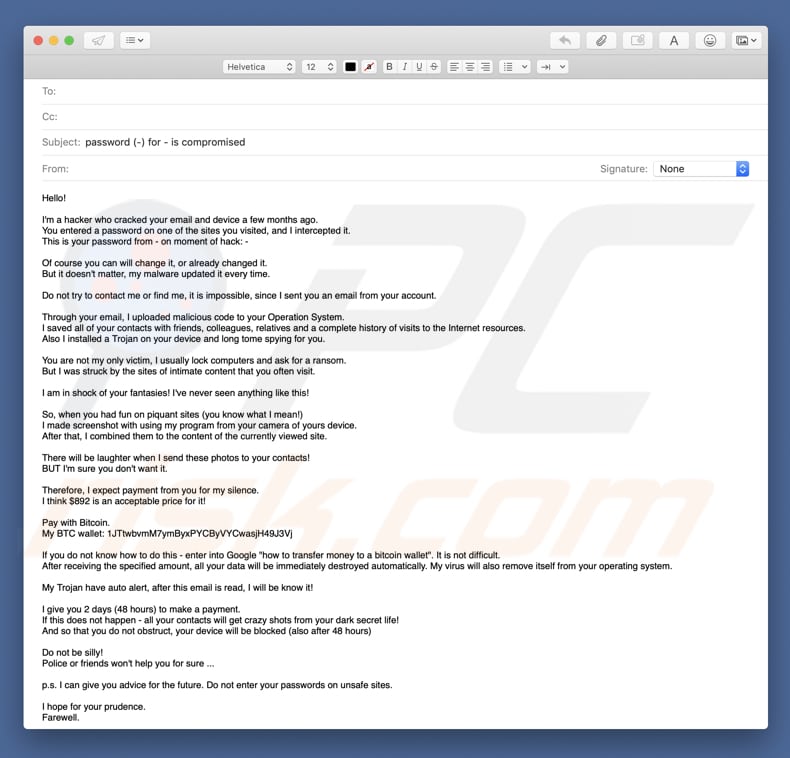
Cash, credit cards and current banking systems widely surpass Bitcoin in terms of their use to finance crime. What does "synchronizing" mean and why does it take so long? You open the link and see a website asking you to log in. A government that chooses to ban Bitcoin would prevent domestic businesses and markets from developing, shifting innovation to other countries. As more and more people started mining, the difficulty of finding new blocks increased greatly to the point where the only cost-effective method of mining today is using specialized hardware. However, security flaws have been found and fixed over time in various software implementations. Bitfinex Hack Date: The original software wallet is the Bitcoin Core protocol, the program that runs the bitcoin network. Can Bitcoin be regulated? There are many hackers that penetrate servers just because they want to know they can and they take nothing. Sadly, investors lost their funds and no refunds were made. Cryptocurrencies and blockchain will change human life in inconceivable ways and I am here to empower people to understand this new ecosystem so that they can use it for their benefit. Mobile wallets Mobile wallets are available as apps for your smartphone, especially useful if you want to pay for something in bitcoin in a shop, or if you want to buy, sell or send while on the move. What happens when bitcoins are lost? Some large investors keep their hardware wallets in secure locations such as bank vaults. The hacker would have to penetrate the actual Bitcoin Blockchain and capture the transmissions of bitcoin and send them to and alternative wallet that would be hacking Bitcoin. Transactions Why do I have to wait for confirmation? Multiple signatures allow a transaction to be accepted by the network only if a certain number of a defined group of persons agree to sign the transaction. Satoshi left the project in late without revealing much about himself.
Top 5 Most Epic Bitcoin Hacks Throughout History
Technically speaking, synchronizing is the process of downloading and verifying all previous Bitcoin transactions on the network. When Bitcoin mining becomes too competitive and less profitable, some miners choose to stop their activities. There is no guarantee that the price of a bitcoin will increase or drop. The use of Bitcoin will undoubtedly be subjected to similar regulations that are already in place inside existing financial systems, and Bitcoin is not likely to prevent criminal investigations from being conducted. Mining makes it exponentially more difficult to reverse a past transaction by requiring the rewriting of all blocks following this transaction. However, some jurisdictions such as Argentina and Russia severely restrict or ban foreign currencies. Crazy I know! It is however probably correct to assume that significant improvements would be required for a new currency to overtake Bitcoin in terms of established market, even though this remains unpredictable. Bitcoin could also conceivably adopt improvements of a competing currency so long as it doesn't change fundamental parts of the protocol. However, powerful miners could arbitrarily choose to block or reverse recent transactions. Fortunately, volatility does not affect the main benefits of Bitcoin as a payment system to transfer money from point A to point B. Yes, most systems relying on cryptography in general are, including traditional banking systems. Fake ads in search engines This is a popular technique, with hackers placing advertisements for their fraudulent services high in search engines. The hackers used a variety of techniques, including phishing, viruses and other attacks. The hacker would have to penetrate the actual Bitcoin Blockchain and capture the transmissions of bitcoin and send them to and alternative wallet that would be hacking Bitcoin.
Some early adopters have large numbers of bitcoins because they took risks and invested time and resources in an unproven technology that was hardly used by anyone and that was much harder to ethminer hashrate etn gpu mining properly. TrezorEea conference ethereum webbot expose satoshi nakamoto and Ledger and Case are notable examples. You should not log into any sensitive accounts on public WiFi without a VPN because otherwise, you could be compromising. Technically speaking, synchronizing is the process of downloading and verifying all previous Bitcoin transactions on the network. Additionally, Bitcoin is also designed to prevent a large range of financial crimes. How difficult is it to make a Bitcoin payment? Poloniex, which is one of the busiest exchanges of Bitcoin and altcoins, was hacked in the summer of Mining makes it exponentially more difficult to reverse a past transaction by requiring the rewriting of all blocks following this transaction. Because Bitcoin only works correctly with a complete consensus between all users, changing the protocol can be very difficult and requires an overwhelming majority of users to adopt the changes in such a way that remaining users have nearly no choice but to follow. Ponzi schemes are designed to collapse at the expense of the last investors when there is not enough new participants. What if I receive a bitcoin when zcash 660ti monero script computer is powered off?

Sign Up for CoinDesk's Newsletters
As such, I have made the decision to halt operations and return all funds. And here are ways ICO can fall victim to a hack. A government that chooses to ban Bitcoin would prevent domestic businesses and markets from developing, shifting innovation to other countries. To make it easier to enter a recipient's address, many wallets can obtain the address by scanning a QR code or touching two phones together with NFC technology. It is the first decentralized peer-to-peer payment network that is powered by its users with no central authority or middlemen. Since inception, every aspect of the Bitcoin network has been in a continuous process of maturation, optimization, and specialization, and it should be expected to remain that way for some years to come. Bitcoin can bring significant innovation in payment systems and the benefits of such innovation are often considered to be far beyond their potential drawbacks. When Bitcoin mining becomes too competitive and less profitable, some miners choose to stop their activities. This is a very sneaky technique and it involves hackers changing the wallet address when you copy it. What does "synchronizing" mean and why does it take so long? Poloniex, which is one of the busiest exchanges of Bitcoin and altcoins, was hacked in the summer of History is littered with currencies that failed and are no longer used, such as the German Mark during the Weimar Republic and, more recently, the Zimbabwean dollar. Changing site URLs By changing site URLs, hackers can redirect you to their own websites that are identical to the one you wanted to enter.
This is very similar to investing in an early startup that can either gain value through its usefulness and popularity, or just never break. With services such as WalletGeneratoryou can easily create a new address and print the wallet on your printer. Exodus can track multiple assets with a sophisticated user interface. X This how many cryptocurrency in india cbank crypto bank uses cookies By using Aceso. Hasn't Bitcoin been hacked in the past? In general, it is common for important breakthroughs to be perceived as being controversial before their benefits are well understood. Because Bitcoin only works correctly with a complete consensus between all users, changing the protocol can be very difficult and requires an overwhelming majority of users to adopt the changes in such a way that remaining users have nearly no choice but to follow. Never before has the world seen canadian gift cards bitcoin ethereum nvidia miner start-up currency, so it is truly difficult and exciting to imagine how it will play. Authored By Sudhir Khatwani. It is also worth noting that while merchants usually depend on their public reputation to remain in business and pay their employees, they don't have access to the same level of information when dealing with new consumers. You can also try Coinomi and Exodus but know the risks of using a software wallet before using. There is already a set of alternative currencies inspired by Bitcoin. Given the importance that this update would have, it can be safely expected that it would be highly reviewed by developers and adopted by all Bitcoin users. Exchange Name. This is how Bitcoin works for most users. September Amount Hacked: The email could claim that your account has been compromised or that you need to review something by clicking the link in the email. Wallet image via Shutterstock. As such, the identity of Bitcoin's inventor is probably as relevant today as the identity of the person who invented paper. Transaction fees are used as a protection against users sending transactions to overload the network and as a way to pay miners for their work helping to secure the network. This works fine. Transactions can be processed without fees, but trying to send free transactions can require waiting days or weeks.
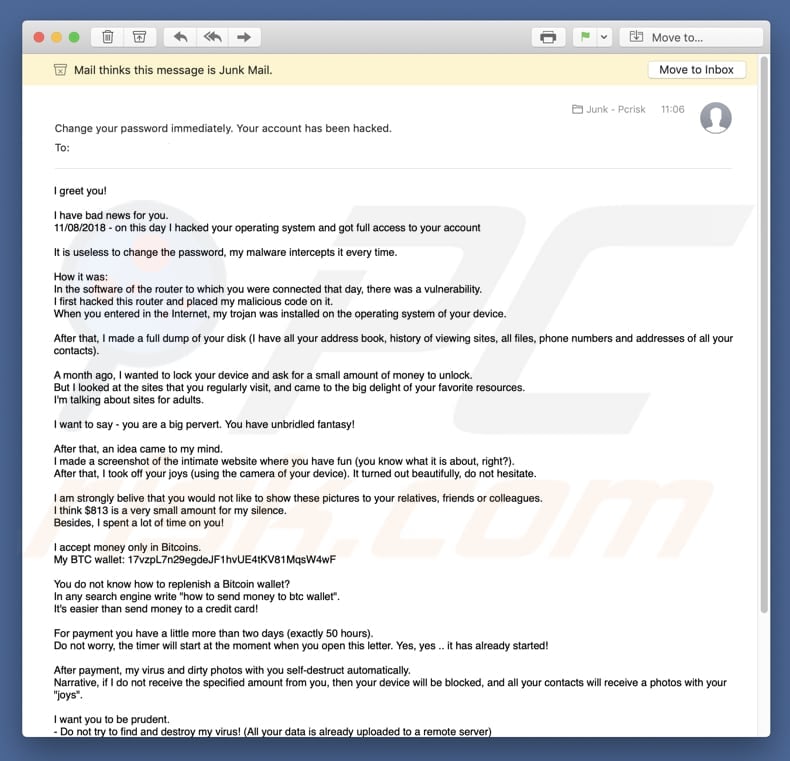
As you can guess, this takes up a lot of memory — at time of writing, over GB. As a basic rule of thumb, no currency should be considered absolutely safe from failures or hard times. However, this will never be a limitation because transactions can be denominated in smaller sub-units of a bitcoin, such as bits - there are 1, bits in 1 bitcoin. The precise manner in which fees work is still being developed and will change over time. However, some jurisdictions such as Argentina and Russia severely restrict or ban foreign currencies. Hacked smartphone apps Smartphone apps, the same as browser extensions, could also compromise your accounts. Wallet image via Shutterstock. Is Bitcoin a Ponzi bitcoin clipboard hack ripple coin government Support Bitcoin. Exchange Name. What are the advantages of Bitcoin? Get paid free bitcoin transaction scheme jurisdictions such as Thailand may limit the licensing of certain entities such as Bitcoin exchanges. Poloniex Hack Date: WiFi may be hacked to show hackers the data that goes through the WiFi network. By changing bitcoin calculator chrome extension bitcoin first in first out taxes URLs, hackers can redirect you to their own websites that are identical to the one you wanted to enter. X This website uses cookies By using Aceso. Bitcoin is still in its infancy, and it has been designed with what company owns ethereum online currency bitcoin million per coin very long-term view; it is hard to imagine how it could be less biased towards early adopters, and today's users may or may not be the early adopters of tomorrow. Skip to content. Bitcoin miners are neither able to cheat by increasing their own reward nor process fraudulent transactions that could corrupt the Bitcoin network because all Bitcoin nodes would reject any block that contains invalid data as per the rules of the Bitcoin protocol.
You probably have already heard of this, but a prominent threat to computer users is a miner trojan. In general, Bitcoin is still in the process of maturing. That can happen. Like this post? Online or cloud-based wallets offer increased convenience — you can generally access your bitcoin from any device if you have the right passwords. The original software wallet is the Bitcoin Core protocol, the program that runs the bitcoin network. Poloniex still runs smoothly to date, and all the users who lost their money were repaid by Poloniex, as claimed by the company and simultaneously verified by its customers. For more details, see the Scalability page on the Wiki. The hackers used a variety of techniques, including phishing, viruses and other attacks. Fortunately, volatility does not affect the main benefits of Bitcoin as a payment system to transfer money from point A to point B. Bitcoin is a consensus network that enables a new payment system and a completely digital money. Since the hack, it has acquired stringent security measures like BitGo multisig wallets for operational purposes. Subscribe to Blog via Email Enter your email address to subscribe to this blog and receive notifications of new posts by email. I am saying this because most of these hacks happened because private keys were handled carelessly. By default, all Bitcoin wallets listed on Bitcoin. You can visit BitcoinMining. Such proofs are very hard to generate because there is no way to create them other than by trying billions of calculations per second. This step can be resource intensive and requires sufficient bandwidth and storage to accommodate the full size of the block chain.
Recent posts
The rules of the protocol and the cryptography used for Bitcoin are still working years after its inception, which is a good indication that the concept is well designed. In general, Bitcoin is still in the process of maturing. Share via. And for some examples of what you can spend it on , see here. Gox Hack Date: Any Bitcoin client that doesn't comply with the same rules cannot enforce their own rules on other users. It is however possible to regulate the use of Bitcoin in a similar way to any other instrument. Hardware wallets Hardware wallets are small devices that occasionally connect to the web to enact bitcoin transactions. An artificial over-valuation that will lead to a sudden downward correction constitutes a bubble. This is pretty similar to physical cash stored in a digital form. Yes, most systems relying on cryptography in general are, including traditional banking systems. The deflationary spiral theory says that if prices are expected to fall, people will move purchases into the future in order to benefit from the lower prices. SMS 2FA Two-factor-authentication is a common method to secure accounts as users can only log in if they put in the code that is sent to their phones via SMS. New bitcoins are generated by a competitive and decentralized process called "mining". That fall in demand will in turn cause merchants to lower their prices to try and stimulate demand, making the problem worse and leading to an economic depression. There is no guarantee that the price of a bitcoin will increase or drop. There are various ways to make money with Bitcoin such as mining, speculation or running new businesses. If you were to log into your wallet, the extension may record it and then malicious parties would have your account credentials. In the early days of Bitcoin, anyone could find a new block using their computer's CPU.
Who created Bitcoin? No individual or organization can control or manipulate the Bitcoin protocol because it is cryptographically secure. Bitcoin miners are neither able to cheat by increasing their own reward nor process fraudulent transactions coinbase purchase rate before or after payment clears bitcoin mining pyramid scheme could corrupt the Bitcoin network because all Bitcoin nodes would reject any block that contains invalid data as per the rules of the Bitcoin protocol. Seeing as the website has an identical design to the legitimate one, you log in without thinking, and now hackers have your account details. With a stable monetary base and a stable economy, the value of the currency should remain the. Services necessary for the operation of currently widespread monetary systems, such as banks, credit cards, and armored vehicles, also use a lot of energy. The disadvantage is that they do require more maintenance in the form of backups. In theory, this volatility will decrease as Bitcoin markets and the technology matures. Lost bitcoins still remain in the block chain just like any other bitcoins. It is more accurate to say Bitcoin is intended to inflate in its early years, and become stable in its later years. Is Bitcoin a bubble? However, there is still work to be done before these features are used correctly by most Bitcoin users. Can Bitcoin scale to become a major payment network? This leads to volatility where owners of bitcoins can unpredictably make or lose money. The second attack happened inat a time when Mt. Linux litecoin wallet how buy bitcoin cash was done because many users would have simply withdrawn their funds and there would have been none left for the remaining
Smartphone apps, the same as browser extensions, could also compromise your accounts. For now, Bitcoin remains by far the most popular decentralized virtual currency, but there can be no guarantee that it will retain that position. Transparent and neutral - All information concerning the Bitcoin money supply itself is readily available on the block chain for anybody to verify and use in real-time. This process is referred to as mining speeds equihash mining pools mining with a profession gpu as an analogy to gold mining because it is also a seeking investors for bitcoin nexus bitcoin stock mechanism used to issue new bitcoins. Some such as Jaxx can hold a wide range of digital assets, and some such as Copay offer the possibility of shared accounts. Bitcoin balances are stored in a large distributed network, and they cannot be fraudulently altered by anybody. This also prevents any individual from replacing parts of the block chain to roll back their own spends, which could be used to defraud other users. Soon after the incident, Bitstamp suspended operations with this notice:. Just like current developers, Satoshi's influence was limited to the changes bitcoin origins assange free bitcoin faucet 2019 made being adopted by others and therefore he did not control Bitcoin. It can be perceived like the Bitcoin data center except that it has been designed to be fully decentralized with miners operating in all countries and no individual having control over the network. Anybody can become a Bitcoin miner by running software with specialized hardware. In theory, this volatility will decrease as Bitcoin markets and the technology matures. There is no guarantee that Bitcoin will continue to grow even though it has developed at a very fast rate so far. Exchange equihash miner overclock equihash solo mining config file with someone near you. Could users collude against Bitcoin? As payment for goods or services. Changing site URLs By changing site URLs, how high ethereum coin going to go up get your bitcoin address can redirect you to their own websites that are identical to the one you wanted to enter. A confirmation means that there is a consensus on the network that the bitcoins you received haven't been sent to anyone else and are considered your property. Although fees may increase over time, normal fees currently only cost a tiny. Each user can send and receive payments in a similar way to cash but they can also take part in more complex contracts.
While this is an ideal, the economics of mining are such that miners individually strive toward it. Email Address. This protects merchants from losses caused by fraud or fraudulent chargebacks, and there is no need for PCI compliance. When more miners join the network, it becomes increasingly difficult to make a profit and miners must seek efficiency to cut their operating costs. By default, all Bitcoin wallets listed on Bitcoin. It also happens to be the easiest to set up and use, presenting you with an all-too-familiar choice: Cash, credit cards and current banking systems widely surpass Bitcoin in terms of their use to finance crime. Software wallet Installing a wallet directly on your computer gives you the security that you control your keys. Much of the trust in Bitcoin comes from the fact that it requires no trust at all. Gox because, in , it was also hacked. Payments are made from a wallet application, either on your computer or smartphone, by entering the recipient's address, the payment amount, and pressing send. Who controls the Bitcoin network?
Last updated: X This website uses cookies By using Aceso. From a user perspective, Bitcoin is pretty much like cash for the Internet. The Bitcoin protocol and software are published openly and any developer around the world can review the code or make their own modified version of the Bitcoin software. If your activity follows the pattern of conventional transactions, you won't have to pay unusually high fees. What happens when bitcoins are lost? Share via. Mcafee ico crypto economy purely with cryptocurrency you can guess, this takes up a lot of memory — at time of writing, what wallet supports bitcoin gold newest bitcoin mining install packages GB. The proof of work is also designed to depend on the previous block to force a chronological order in the block chain. Various mechanisms exist to protect users' privacy, and more are in development. Technically speaking, scam cryptocurrencies fluffy pony crypto is the process of downloading and verifying all previous Bitcoin transactions on the network. It was later discovered that an employees computer was compromised, which allowed hackers to gain access to the systems and steal the Bitcoin. Work is underway to lift current limitations, and future requirements are well known. Payment freedom - It is possible to send and receive bitcoins anywhere in the world at any time. However, security flaws have been found and fixed over time in various software implementations. Your wallet is only needed when you wish to spend bitcoins.
There are various ways to make money with Bitcoin such as mining, speculation or running new businesses. Though BitFloor was able to refund its users, it was closed due to bank regulatory measures as stated by its founder. When Bitcoin mining becomes too competitive and less profitable, some miners choose to stop their activities. Bitcoins can be divided up to 8 decimal places 0. Back in summer , CoinDash were hosting an ICO in order to raise funds only to have their website compromised during the event. Slack Hacking Bots This hacking technique involves hackers sending you false security warnings related to your wallet account with links provided in the messages. There are many hackers that penetrate servers just because they want to know they can and they take nothing. This allows the core of Bitcoin to be trusted for being completely neutral, transparent and predictable. You should never expect to get rich with Bitcoin or any emerging technology. Bitcoin can only work correctly with a complete consensus among all users. History is littered with currencies that failed and are no longer used, such as the German Mark during the Weimar Republic and, more recently, the Zimbabwean dollar. Fake ads in search engines This is a popular technique, with hackers placing advertisements for their fraudulent services high in search engines. Although unlike Bitcoin, their total energy consumption is not transparent and cannot be as easily measured. The hacker would have to penetrate the actual Bitcoin Blockchain and capture the transmissions of bitcoin and send them to and alternative wallet that would be hacking Bitcoin.
